In my previous article I wrote a few words about the WPAD/LLMNR protocols and gave you an example of how to use wpad to set up an attack. Now, more importantly, here are a few tips on how to protect your network being vulnerable.
Tip #1 – Turn off WPAD on a stand-alone workgroup computer:
In Windows 10, simply un-tick this box, and most modern web browsers should replicate this setting into their browsers advanced settings. Double check settings in your browser to make sure it’s off.

Tip #2 – Turn off WPAD in your enterprise domain using Group Policy:
User Configuration > Windows Components > Internet Explorer:
Disable changing Automatic Configuration settings: Enabled
Prevent changing proxy settings: Enabled
User Configuration > Preferences > Control Panel Settings > Internet Settings:
Right click and make a new rule for IE 10. Go to Connections, LAN settings and make sure “Automatically detect settings” is turned off.
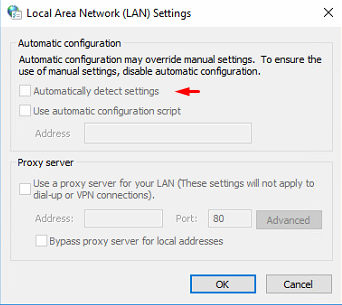
Users will be unable to turn on WPAD. Note that this setting is replicating with Windows 10 proxy-setting, so all browsers should now be safe.
Tip #3 – Make a new entry in DNS for “wpad”:
To be even more bulletproof against any wpad poisoning attacks, you should add a new DNS entry for “wpad”. To make this work, note that Microsoft introduced a new feature called “Global Query Block List” in Windows Server 2008 and later.
This is a list of querys being blocked by the DNS server, introduced purely to prevent malicious clients from registering these names in the dynamic DNS. These names include “wpad” and “isatap”.
To remove “wpad” from the Global Query Block List, open regedit and go to:
HKEY_LOCAL_MACHINE > SYSTEM > CurrentControlSet > Services > DNS > Parameters
In GlobalQueryBlockList, remove wpad entry:

Restart your DNS server, and you should now be able to make a new A record in your DNS pointing to 127.0.0.1. Make sure to set the loopback address, making any wpad requests from a browser pointing to its own local system and not others.
Also note, that if WPAD is enabled in a browser after specifying a wpad DNS entry, the browser will use a few seconds to look for the PAC file locally on that system before the request it’s being discarded and the user is forwarded to any websites.